Copyright Disclaimer Under Section 107 of the Copyright Act 1976?Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favor of fair use. Unless you are in this field of investigative journalism, especially covering extremely sensitive subjects and potentially dangerous subjects as well, you simply cannot understand the complexities and difficulties involved with this work that I face every day.
Friday, February 15, 2013
"MARK OF THE BEAST" hits Pensacola Navy Base?
MARK OF THE BEAST hits Pensacola Navy Base!: http://youtu.be/-_mDvOk6Wvk via @youtube
Federal Agents Raid Virginia Carrier
Federal Agents Raid Virginia Carrier
[ A- ] / [ A+ ]Since 2006, Beam Brothers Trucking has been under investigation by the feds. According to WHSV, affidavits show that workers reported that their supervisors made them lie about the hours they worked and falsify or create new logs.
If drivers refused to falsify their logs, they were threatened with termination or their paychecks were withheld.
One witness claimed a supervisor “told him he needed to falsify his logbooks in order to receive his paycheck, meaning if he drove over the 11 hour rule, he had to make a new logbook and manipulate it to reflect 11 hours of driving. The witness recalled a specific occasion when his paycheck was not direct deposited into his bank account. One or two days later, he received a letter from Bean Brothers Trucking management at his residence, which stated he needed to falsify his logs in order to be paid…the witness stated that after he was involved in an accident, he called a supervisor and told him he was over his hours. The supervisor instructed him to falsify his logbook.”
Seven witnesses complained to authorities that their supervisors made them lie about the hours they worked and falsify their logs. Some employees even claimed they were told to destroy their logbooks when they arrived at their destination and fill out new logs.
This isn’t the first time the carrier has come under fire for HOS and logbook violations.
In 2004, Beam Brothers Trucking was fined $22,670 for 11 HOS violations.
In 2010, Beam Brothers Trucking was fined $31,480 for 23 violations of “false reports of duty status” and 16 violations for “failure to preserve driver’s records of duty status supporting documents for six months.” Beam Brothers settled the charges and paid a $25,000 fine
Read more at http://cdllife.com/2013/top-trucking-news/federal-agents-raid-virginia-carrier/#IkWd0XhkkvcWlbr3.99
Defendant himself posted his tax returns on the public web site WhiteHouse.gov, one of the most travelled web sites in the world and did not flattened the PDF file, therefore full, unredacted Connecticut Social Security xxx-xx-4425, which he used in conjunction to his 2009 Tax Returns became available to millions of the U.S. citizens and citizens around the world. This Social Secuirty failed both E-Verify and SSNVS (Social Security Number Verification Systems), two systems of verification of the Social Security number, showing that the number that the Defendant is using in his tax returns was never issued to him. This represents Social Security Fraud, Identity fraud and Elections Fraud as defendant ran for the highest office in the U.S. government without possessing a valid Social security number, one of the two basic Identification papers used in the United States of America
Defendant himself posted his tax returns on the public web site
WhiteHouse.gov, one of the most travelled web sites in the world and did
not flattened the PDF file, therefore full, unredacted Connecticut
Social Security xxx-xx-4425, which he used in conjunction to his 2009
Tax Returns became available to millions of the U.S. citizens and
citizens around the world. This Social Secuirty failed both E-Verify and
SSNVS (Social Security Number Verification Systems), two systems of
verification of the Social Security number, showing that the number that
the Defendant is using in his tax returns was never issued to him. This
represents Social Security Fraud, Identity fraud and Elections Fraud as
defendant ran for the highest office in the U.S. government without
possessing a valid Social security number, one of the two basic
Identification papers used in the United States of America
Based on all of the above Default Judgment is GRANTED. This court is forwarding its findings to the Chairman of the Judiciary Commission of the U.S. Congress for determination whether the Articles of impeachment against Defendant BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH are justified.
Based on all of the above Default Judgment is GRANTED. This court is
forwarding its findings to the Chairman of the Judiciary Commission of
the U.S. Congress for determination whether the Articles of impeachment
against Defendant BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA
BARACK (BARRY) OBAMA SOEBARKAH are justified.
Based on the unrefuted evidence by the Plaintiffs this court makes a finding and Declaratory ruling that Defendant BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH was not eligible to the position of the U.S. President and Commander in Chief as he is a citizen of Indonesia, who ran for the U.S. Presidency based on fraud and misrepresentation and using either forged or fraudulently obtained identification papers.
Based on the unrefuted evidence by the Plaintiffs this court makes a
finding and Declaratory ruling that Defendant BARACK HUSSEIN OBAMA, AKA
BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH was not
eligible to the position of the U.S. President and Commander in Chief as
he is a citizen of Indonesia, who ran for the U.S. Presidency based on
fraud and misrepresentation and using either forged or fraudulently
obtained identification papers.
…Breaking news! Defendant Barack Obama defaulted in Grinols et al v Obama et al. Notice of Default filed
…Breaking news! Defendant Barack Obama defaulted in Grinols et al v Obama et al. Notice of Default filed
Press ReleaseLaw office of Orly Taitz
Defendant Barack Obama defaulted in Grinols et al v Obama et al. Notice of default filed, expedite default judgment requested.
Grinols Notice of Default of Defendant Obama
Notice of Electronic Filing
The following transaction was entered by Taitz, Orly on 1/30/2013 at 8:14 PM PST and filed on 1/30/2013
Docket Text: NOTICE Notice of DEFAULT of DEFENDANT Obama, request for an expedited DEFAULT Judgment and post judgment discovery by All Plaintiffs. (Taitz, Orly)
2:12-cv-02997-MCE-DAD Notice has been electronically mailed to:
Edward A Olsen , GOVT edward.olsen@usdoj.gov, karen.james@usdoj.gov, monica.lee@usdoj.gov, teisha.stogsdill@usdoj.gov
George Michael Waters george.waters@doj.ca.gov, lydia.sandoval@doj.ca.gov
Orly Taitz orly.taitz@gmail.com, dr_taitz@yahoo.com
2:12-cv-02997-MCE-DAD Electronically filed documents must be served conventionally by the filer to:
Dr. Orly Taitz ESQ| Case Name: | Grinols et al v. Electoral College et al |
| Case Number: | 2:12-cv-02997-MCE-DAD |
| Filer: | James Grinols |
| Keith Judd | |
| Thomas Gregory MacLeran | |
| Edward Noonan | |
| Robert Odden | |
| Document Number: | 64 |
2:12-cv-02997-MCE-DAD Notice has been electronically mailed to:
Edward A Olsen , GOVT edward.olsen@usdoj.gov, karen.james@usdoj.gov, monica.lee@usdoj.gov, teisha.stogsdill@usdoj.gov
George Michael Waters george.waters@doj.ca.gov, lydia.sandoval@doj.ca.gov
Orly Taitz orly.taitz@gmail.com, dr_taitz@yahoo.com
2:12-cv-02997-MCE-DAD Electronically filed documents must be served conventionally by the filer to:
The following document(s) are associated with this transaction:
Document description:Main Document Original filename:n/a Electronic document Stamp: [STAMP dcecfStamp_ID=1064943537 [Date=1/30/2013] [FileNumber=5951932-0 ] [99d8319f28ecde09f487b404ac329fd4f73ab3686d082711ed46399b174fcfceffa 05bd43535b2382241da21cfca3e458c187091127b9ed9bb688a5c9f99773e]]
Document description:Main Document Original filename:n/a Electronic document Stamp: [STAMP dcecfStamp_ID=1064943537 [Date=1/30/2013] [FileNumber=5951932-0 ] [99d8319f28ecde09f487b404ac329fd4f73ab3686d082711ed46399b174fcfceffa 05bd43535b2382241da21cfca3e458c187091127b9ed9bb688a5c9f99773e]]
29839 Santa Margarita, ste 100
Rancho Santa Margarita, Ca 92688
949-683-5411 fax 949-766-7603
Orly.taitz@gmail.com
IN THE US DISTRICT COURT FOR THE EASTERN DISTRICT OF CALIFORNIA
Grinols et al ) Case # 12-cv-2997
V ) Honorable Morrison C. England
Electoral College et al ) Chief Judge Presiding
NOTICE OF DEFAULT OF DEFENDANT BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH
REQUEST FOR AN EXPEDITED DEFAULT JUDGMENT AND A PROPOSED DEFAULT JUDGMENT
Case at hand was file on 12.12.2012. Defendant BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH was sued in his capacity as a candidate for the U.S. President. Defendant was served by Same Day professional service processer on 01. 04.2013. Defendant was under an obligation to file an answer or a responsive pleading within 21 days on 01.25.2013. Defendant failed to file an answer or a responsive pleading and is currently in DEFAULT.
Plaintiffs are hereby respectfully requesting a default judgment against the defendant, post judgment discovery, costs and attorney fees. Additionally, Plaintiffs are seeking an EXPEDITED DEFAULT JUDGMENT for the following reason:
Commissioner of Social Security, Bush appointee is Michael Astrue. He announced that he is leaving office in February, within days. According to evidence provided to this court, Obama made his tax returns public, which show him using a CT SSN xxx-xx-4425, which was never assigned to him according to E-Verify and SSNVS. Affidavits of investigators Sankey and Daniels already submitted to this court with the complaint, show aforementioned SSN to be linked in a number of databases to a date of birth 1890.
Recently investigator Albert Hendershot found in the database of http://www.acxiom.com/identity-solutions/acxiom-identity-batch-solutions/ the name of the individual whose Social Security Obama is using. Acxciom-batch-solutions showed (Exhibit 1) that Harry J Bounel with the same Social Security number xxx-xx-4425 at 5046 S Greenwood Ave in Chicago, home address of Barack Obama, Database shows Bounel with the same address and Social Security number as Barack Obama himself. According to the databases last changes to the information on Harrison(Harry) J Bounel were made in and around November 2009 by Michelle Obama, who is listed as Bounel’s relative. Database changes can involve entering the information or deletion of information. It appears that changes made by relative Michelle Obama included deletion of information, which was done at a time when Taitz brought to Federal court in the Central District of California before Judge David O. Carter a case of election challenge by her client, former U.S. ambassador Dr. Alan Keyes and 40 state Representatives and high ranked members of the U.S. military.
Recently obtained results of the 1940 census, Exhibit 2, provided the last missing link, link between Harry J. Bounel and the date of birth of 1890. Exhibit 2 shows the printout of the U.S. census, showing Harry J Bounel, immigrant from Russia, residing at 915 Daly Ave, Bronx, NY, age 50 during the 1940 census, meaning he was born in 1890, as shown in the affidavit of Investigators Daniels and Sankey.
There is a pattern of Obstruction of Justice and tampering with the official records and falsification/forgery of the official records related to Obama. This happens in particular when Bush employees leave their positions and are replaced by Obama appointees.
In March of 2009 one of the clients of Taitz, Major General Carol Childers arranged for her to meet with the Director of the Selective Service William Chatfield. After Taitz provided Chatfield with evidence of forgery of Obama’s alleged Selective Service certificate, Childers resigned and was replaced by Obama appointee Lawrence Romo. Later, when Sheriff of Maricopa county, AZ Joseph Arpaio demanded from Romo the original paper registration by Obama, Romo responded that it was destroyed.
Similarly, when the former intelligence officer Pamela Barnett sought passport records of Stanley Ann Dunham, Obama’s mother, she was given only some of the records and was told that the 1965 passport for Dunham was destroyed.
When investigator Sandler provided Taitz and reporter Corsi with a batch number for the immigration/travel records for Obama for August 1-7 1961, those records disappeared from the National Archives, even though the records for the other 51 weeks for 1961 could be found with no problem. After an article was written about missing records, there was a falsification of records and another investigator, Montgomery Blair Sidley found a record, where original date of August 7, 1961 was visibly erased and August 1, 1961 was written over it (Exhibit 3).
Based on the pattern of the original vital records, which are essential in removing Obama from office and criminally prosecuting him, rapidly disappearing, there is a high probability that the SSA application SS-5 for the Social Security number for Harry J. Bounel will be either destroyed or falsified the moment Bush appointee Commissioner of Social Security Astrue leaves in February and is replaced by the Obama appointee. Due to high probability of essential evidence being destroyed or altered Plaintiffs are asking this court to issue and expedited Default Judgment against the Defendant Obama, aka Soetoro, aka Soebarkah and order expedited post judgment discovery, which should include the production of the original SS-5 for the Connecticut SSN xxx-xx-4425.
Respectfully submitted
/s/ Dr. Orly Taitz ESQ
Attorney for Plaintiffs
CC.
UN Nations committee for civil rights defenders
OHCHR in New York
UN Headquarters
New York, NY 10017
USA
Inter-American Commission for Human rights
1889 F St., NW,
Washington, D.C., USA 20006
Darrel Issa
Chairman of the House oversight committee
2157 RAYBURN HOUSE OFFICE BUILDING,
WASHINGTON, DC 20515
Congressman Bob Goodlatt ,
Chairman of the Judiciary Committee
House of Representative
2409 2157 RAYBURN HOUSE OFFICE BUILDING,
WASHINGTON, DC 20515
PROPOSED ORDER
Case at hand was file on 12.12.2012. Defendant BARACK HUSSEIN OBAMA,
AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH was sued
in his capacity as a candidate for the U.S. President. Defendant was
served by SameDay professional service processer on 01. 04.2013.
Defendant was under an obligation to file an answer or a responsive
pleading within 21 days on 01.25.2013. Defendant failed to file an
answer or a responsive pleading and is currently in DEFAULT.Complaint and 100 exhibits provided by the Plaintiffs provided the following evidence, which was not refuted by the Defendant:
- Defendant Obama never lawfully registered with the Selective Service and the selective service registration represents a computer generated forgery and as such defendant is not eligible to work in any position in the executive branch of the U.S. Government, which of course includes the Chief Executive- The U.S. President and the Commander in Chief of the U.S. military. (Sworn Affidavit of Jeffrey Stephan Coffman, the Chief Investigator of the Special investigations Unit of the U.S. Coast Guard (ret) and former special agent of the U.S. Department of the Homeland Security). As such Obama fraudulently submitted his candidacy for the U.S. President, while knowing all along that he is not eligible for any position in the Executive Branch.
- Defendant fraudulently ran for the position of the U.S. President while using the last name Obama, while in his mother’s passport records he is listed under the legal name Soebarkah. As such Barack Obama was unlawfully elected, confirmed by the U.S. Senate and sworn in by the Chief Justice John Roberts, as legal entity “Barack Obama” does not exist. Defendant failed to provide any proof of legal change of name from Soebarkah to Obama.
- Plaintiffs provided this court with the copy of the School registration of the Defendant from the Assissi School in Jakarta, Indonesia, where his citizenship is listed as Indonesian. Defendant failed to provide any evidence of Change of Citizenship from Indonesian to American. Even if he were to legally relinquish his Indonesian citizenship to American upon his arrival from Indonesia in 1971, he would be a Naturalized Citizen and not Natural born as required by the Article 2, Section 1, Clause 5 of the U.S. Constitution.
- OCON, official certification of Candidate signed by the Chairman of the Democratic Party of Hawaii Brian Schatz(recently appointed to the U.S. Senator from HI) and the secretary of the Democratic Party of Hawaii Lynn Matusow was a flagrantly falsified document, as required wording “eligible according to provisions of the U.S. Constitution” was removed from the Certification, whereby there was never a valid certification of the candidate, which showed an intent to defraud and fraud on the part of the Defendant and aforementioned executives of the Democratic Party of Hawaii.
- Defendant himself posted his tax returns on the public web site WhiteHouse.gov, one of the most travelled web sites in the world and did not flattened the PDF file, therefore full, unredacted Connecticut Social Security xxx-xx-4425, which he used in conjunction to his 2009 Tax Returns became available to millions of the U.S. citizens and citizens around the world. This Social Secuirty failed both E-Verify and SSNVS (Social Security Number Verification Systems), two systems of verification of the Social Security number, showing that the number that the Defendant is using in his tax returns was never issued to him. This represents Social Security Fraud, Identity fraud and Elections Fraud as defendant ran for the highest office in the U.S. government without possessing a valid Social security number, one of the two basic Identification papers used in the United States of America
- Plaintiffs provided sworn affidavits of Sheriff Joseph Arpaio, Investigator Mike Zullo, Typesetting expert Paul Irey, Adobe-Illustrator/Computer Graphics expert Felicito Papa, scanning machines expert Douglas Vogt and others, which show that the alleged copy of Barack Obama’s alleged long form birth certificate represents a computer generated forgery, while Department of Health of Hawaii refused to comply with any and all federal and state subpoenas and never provided to any judge or jury or expert an original birth certificate that they claim to possess. At this point there is no reason to believe that the original 1961 type written birth certificate ever existed, as there would not have been a reason to create a flagrant forgery, if an original birth certificate ever existed.
- Based on all of the above Default Judgment is GRANTED. This court is forwarding its findings to the Chairman of the Judiciary Commission of the U.S. Congress for determination whether the Articles of impeachment against Defendant BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH are justified.
- Based on the unrefuted evidence by the Plaintiffs this court makes a finding and Declaratory ruling that Defendant BARACK HUSSEIN OBAMA, AKA BARACK (BARRY) SOETORO, AKA BARACK (BARRY) OBAMA SOEBARKAH was not eligible to the position of the U.S. President and Commander in Chief as he is a citizen of Indonesia, who ran for the U.S. Presidency based on fraud and misrepresentation and using either forged or fraudulently obtained identification papers.
- Plaintiff are entitled to their costs, attorneys fees and post judgment discovery.
So ORDERED and ADJUDGED on this ____________________________________ of __________
Chief Judge U.S District Court of
Obama Goes Back To The Supreme Court Of The U.S. February 15, 2013: Fake IDs!
Obama Goes Back To The Supreme Court Of The U.S. February 15, 2013: Fake IDs!
By Volubrjotr on
Breaking News – US Supreme Court To Hear Case Against Obama Fraud In A Closed Door Hearing Away From The Main Stream Media Spotlight
OBAMA TRIAL 15 FEB 2013 IN US SUPREME COURT –OVER OBAMA USING FAKE ID– FAKE SOC SEC NUMBER 042-68-4425 –FAKE DRAFT CARD- WITH FAKE POSTAL STAMP.–JUSTICE ROBERTS PUT THE OBAMA TRIAL BEHIND CLOSED DOORS –TREASONOUS– CONGRESS OPEN THE OBAMA TRIAL TO THE PUBLIC NOW.
- Barack Obama Not Commander In Chief Of The Military: Detailed Dying For The Banking Cabal.
- Obama Has Proven That The Executive Branch Can No Longer Exist When As A Lone Wolf He Disregards The Constitution: Petition For Psychiatric Evaluation Of Presidential Candidates.
- “We The People” Of The United States Must Assert Our Sovereignty!
Orly Taitz, friend of The Obama Hustle will have her case against the protected one on the 15th of this month. In a hearing behind closed doors which is unheard of as far as I can tell, Taitz will have her day with the Justices. She will be using information supplied by the Obama Hustle detailing the frauds committed byBarack Obama along with other evidence supplied by experts and others across the spectrum of various expertise.
She will be using evidence supplied by my article:
http://theobamahustle.wordpress.com/2013/01/23/breaking-news-obama-caught-using-stolen-social-security-number/ which details Obama’s crime in detail and finally connected the dots on his crime against the American people with the theft of the social security number that he stole from Harry Bounel, a man from Russia born in 1890.
Like her or not, people have to respect Orly’s tenacity in digging for the truth and shedding light on the protected one and his many crimes such as:If VP and cabinet failed to bring him to justice, then Congress fails the Supreme Court, If the Court fails then the military, if military fails then the States, if they fail then the Peoples militia.
- A fraudulent and forged Birth Certificate
- Stolen social security number
- Real Estate fraud
- Tax fraud
- High Crimes and against the American people
- Election fraud
- A forged Selective Service document
- Aliases
- 2006 US Senate Ethics violations
This article clearly details how in 2006 Obama committed a US Senate Ethics violation by not disclosing a $104,500.00 reale state transaction that was a separate business transaction from his supposed real property, ie his home in IL. http://theobamahustle.wordpress.com/2011/08/17/obama-caught-lying-on-his-2006-u-s-senate-financial-disclosure-report/
This article clearly lays out the crime committed by Obama and the social security fraud that he committed when he stole Harry Bounel’s social security number. http://theobamahustle.wordpress.com/2011/09/13/three-strikes-on-obamas-bogus-social-security-number/
This article clearly lays out in detail through a FOIA request from Cook County, IL which details Obama’s real estate fraud committed in 2005 when that house in Chicago was purchased for him to live in. http://theobamahustle.wordpress.com/2011/10/03/documents-recived-through-the-freedom-of-information-act-from-cook-county-treasurers-office-prove-fraud-in-obama-buffer-zone/
This article clearly details the many addresses that Obama used to commit his voter fraud in 2008. http://theobamahustle.wordpress.com/2011/05/24/report-iv-address-search-for-barack-obama-in-a-50-state-search/
This article clearly proves that Congress knows about the inconsistencies / fraud that surround Obama and how they are afraid to go after him for fear of being labeled as radicals by the MSM. http://theobamahustle.wordpress.com/2012/03/11/rep-posey-spokesman-media-ridicule-stopping-us-from-addressing-obamas-identity-fraud/?preview=true&preview_id=1016&preview_nonce=7de4ca725b
It is amazing how Congress and the MSM refuse to open the discussion on the so-called inconsistencies / fraud that surround this individual.
In 2011 I performed a live database pull which was actually seen by the office of FL Congressman Bill Posey which clearly proved that Obama has an alias and that he is in fact using a stolen social security number which has now been proven to belong to an individual by the name of Harry Bounel as proven by a SSA FOIA received in November of 2012.
The US Congress and the MSM need to go after the criminal Obama and investigate him the way they did when Nixon was caught committing crimes within the Watergate investigation. Barack Obama is fraud who has lied to the American people and the MSM along with the US Congress are complicit in this deceit on the United States of America.
The Obama Hustle
Related articles
- Aliases Obama allegedly used are Barry Soetoro, Harrison J. Bounel, entering Obama’s claimed Social Security number (042-68-4425) (charlesoliverblog.wordpress.com)
- Orly Taitz – Takes case against Obama to Supreme Court (usazorrozpress.wordpress.com)
- Breaking News! Chief District Judge to rule whether there will be a Temporary Restraining Order enjoining certification of Obama’s election (theobamahustle.wordpress.com)
- Breaking News! Chief Justice of the Supreme Court John Roberts Schedules a Case by Attorney Taitz Regarding Obama’s Forged Ids to Be Heard in Conference Before the Full Supreme Court(theobamahustle.wordpress.com)
- Supreme Court Conference Scheduled For Obama Forged ID’s (youviewed.com)
- PAPERS PLEASE: Supreme Court To Review Obama Forged Documents (secretsofthefed.com)
- Breaking News – Obama Caught Using Stolen Social Security Number (theobamahustle.wordpress.com)
- Birther News-CA Judge Reinstates Obama Eligibility Lawsuit: Identity Document Fraud & Election Fraud(themadjewess.com)
- Politics & NWO - Re: JUST IN- OBAMA BIRTH CERTIFICATE (disclose.tv)
- Obama’s Alias of “Harry Bounel” Found in 1940 Census (wtpotus.wordpress.com)
- Aliases Obama allegedly used are Barry Soetoro, Harrison J. Bounel, entering Obama’s claimed Social Security number (042-68-4425) (charlesoliverblog.wordpress.com)
- Colonel Sellin ~ Only Rebellion Against Corporate Tyranny Can Save America! (politicalvelcraft.org)
- Obama birther scandal: Appeals court reinstates case against president (Photos) (examiner.com)
- Breaking News – Obama Caught Using Stolen Social Security Number (theobamahustle.wordpress.com)
- Breaking News – US Supreme Court To Hear Case Against Obama Fraud In A Closed Door Hearing Away From The Main Stream Media Spotlight (theobamahustle.wordpress.com)
- Chief Justice Roberts has scheduled a conference hearing on Obama eligibility case brought by Orly Taitz (servehiminthewaiting.wordpress.com)
- PAPERS PLEASE: Supreme Court To Review Obama Forged Documents (secretsofthefed.com)
- Politics & NWO – Re: JUST IN- OBAMA BIRTH CERTIFICATE (disclose.tv)
- Obama not above the law: Supreme Court hearing case against Obama and Sheriff Arpaio’s Investigation continues (moralmatters.org)
MEDIA BLACKOUT: Obama Forged IDs & Eligibility "Heard in Conference" Before the Full Supreme Court... T O D A Y !
MEDIA BLACKOUT: Obama Forged IDs & Eligibility "Heard in Conference" Before the Full Supreme Court... T O D A Y !

Chief
Justice John Roberts Schedules A Case Regarding Obamas Forged IDs to be
Heard in Conference Before the Full Supreme Court. Date: FEBRUARY 15,
2013.
The case titled Noonan, Judd, MacLeran, Taitz v Bowen provides a mountain of evidence of Barack Obama using a last name not legally his, forged Selective Service application, forged long form and short form birth certificate and a Connecticut Social Security number 042-68-4425 which was never assigned to him according to E-Verify and SSNVS. Additionally, this case provides evidence of around one and a half million invalid voter registrations in the state of California alone.
More from Huffington Post: Taitz's case argues that Obama is using false identification, a fake last name, a false Social Security number and forged birth certificates, and Selective Service applications to run for president. She originally filed the lawsuit against California Secretary of State Debra Bowen (D) in her attempt to prevent California's electoral votes from being counted and to prevent Vice President Joe Biden from counting the electoral votes earlier this month.
A federal judge in California dismissed this case last week. Taitz likened her current case to Watergate.
"Please, keep in mind, Richard Nixon was reelected and sworn in, but later was forced to resign as a result of Watergate. over 30 high ranking officials of Nixon administration including Attorney General of the United States and White House Counsel were indicted, convicted and went to prison," Taitz wrote on her website.
"ObamaForgery gate is a hundred times bigger then Watergate. More corrupt high ranking officials, US Attorneys, AGs and judges were complicit, committed high treason by allowing a citizen of Indonesia and possibly still a citizen of Kenya Barack Hussein Obama, aka Barack (Barry) Soebarkah, aka Barack (Barry) Soetoro to usurp the U.S. Presidency by use of forged IDs and a stolen Social security number."
SCOTUS printout is below. For more information on this
and other cases please, go to web site OrlyTaitzESQ.com. Attorney Taitz can be contacted at orly.taitz@gmail.com, fax-949-766-7603. In case of an emergency only she can be contacted by phone 949-683-5411
Follow us: @redflagnews on Twitter
The case titled Noonan, Judd, MacLeran, Taitz v Bowen provides a mountain of evidence of Barack Obama using a last name not legally his, forged Selective Service application, forged long form and short form birth certificate and a Connecticut Social Security number 042-68-4425 which was never assigned to him according to E-Verify and SSNVS. Additionally, this case provides evidence of around one and a half million invalid voter registrations in the state of California alone.
More from Huffington Post: Taitz's case argues that Obama is using false identification, a fake last name, a false Social Security number and forged birth certificates, and Selective Service applications to run for president. She originally filed the lawsuit against California Secretary of State Debra Bowen (D) in her attempt to prevent California's electoral votes from being counted and to prevent Vice President Joe Biden from counting the electoral votes earlier this month.
A federal judge in California dismissed this case last week. Taitz likened her current case to Watergate.
"Please, keep in mind, Richard Nixon was reelected and sworn in, but later was forced to resign as a result of Watergate. over 30 high ranking officials of Nixon administration including Attorney General of the United States and White House Counsel were indicted, convicted and went to prison," Taitz wrote on her website.
"ObamaForgery gate is a hundred times bigger then Watergate. More corrupt high ranking officials, US Attorneys, AGs and judges were complicit, committed high treason by allowing a citizen of Indonesia and possibly still a citizen of Kenya Barack Hussein Obama, aka Barack (Barry) Soebarkah, aka Barack (Barry) Soetoro to usurp the U.S. Presidency by use of forged IDs and a stolen Social security number."
SCOTUS printout is below. For more information on this
and other cases please, go to web site OrlyTaitzESQ.com. Attorney Taitz can be contacted at orly.taitz@gmail.com, fax-949-766-7603. In case of an emergency only she can be contacted by phone 949-683-5411
Follow us: @redflagnews on Twitter
No. 12A606
Title:
.
.
Docketed:
Lower Ct:
Case Nos.:
Title:
.
.
Docketed:
Lower Ct:
Case Nos.:
.
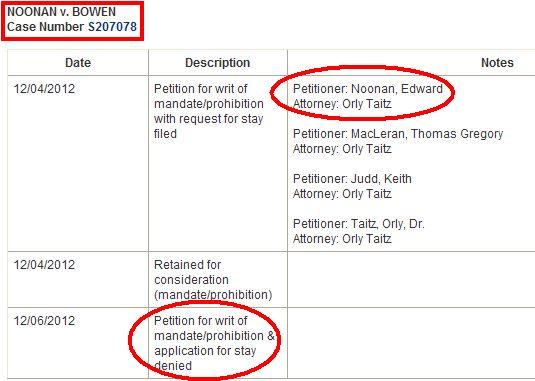
Edward Noonan, et al., Applicants
v.
Deborah Bowen, California Secretary of State
December 13, 2012
Supreme Court of California
(S207078)
Edward Noonan, et al., Applicants
v.
Deborah Bowen, California Secretary of State
December 13, 2012
Supreme Court of California
(S207078)
Date
Dec 11 2012
Dec 13 2012
Dec 26 2012
Jan 9 2013
Jan 9 2013
Dec 11 2012
Dec 13 2012
Dec 26 2012
Jan 9 2013
Jan 9 2013
Proceedings and Orders
Application (12A606) for a stay, submitted to Justice Kennedy.
Application (12A606) denied by Justice Kennedy.
Application (12A606) refiled and submitted to The Chief Justice.
DISTRIBUTED for Conference of February 15, 2013.
Application (12A606) referred to the Court.
Application (12A606) for a stay, submitted to Justice Kennedy.
Application (12A606) denied by Justice Kennedy.
Application (12A606) refiled and submitted to The Chief Justice.
DISTRIBUTED for Conference of February 15, 2013.
Application (12A606) referred to the Court.
Follow us: @redflagnews on Twitter

Obama Calls Egypt’s Muslim Brotherhood President, Tells Him He “Rejects Efforts To Denigrate Islam”
Obama Calls Egypt’s Muslim Brotherhood President, Tells Him He “Rejects Efforts To Denigrate Islam”
Weasel Zippers ^ | September 13, 2012 | Zip
Posted on Thursday, September 13, 2012 9:31:34 AM by CaptainKrunch
Apologizing for our First Amendment rights?

Weasel Zippers ^ | September 13, 2012 | Zip
Posted on Thursday, September 13, 2012 9:31:34 AM by CaptainKrunch
Apologizing for our First Amendment rights?
this is what i am sending to the fbi copy patse what ever send to your fbi to report obama too
the muslim brother hood is on your terrorist list why is obama one of them why aint you arrested him Levin: Hagel Proves Obama Musli… http://freethoughtblogs.com/dispatches/2013/02/05/levin-hagel-proves-obama-muslim-brotherhood-infiltration/ Mark Levin Explodes: 'The Muslim Brotherhood Has Infiltrated Our Gov't — It's Called Barack Obama' http://www.mediaite.com/tv/mark-levin-explodes-the-muslim-brotherhood-has-infiltrated-our-govt-its-called-barack-obama/ via @mediaite Political Brambles: "I Am One Of You" Obama Said To The Muslim Brother... http://politicalbrambles.blogspot.com/2013/02/i-am-one-of-you-obama-said-to-muslim.html?spref=tw Man at Pro-Second Amendment Rally Exposing the Obama Administration, Dri...: http://youtu.be/C_tVU0AmaQk via @youtube THE TRUTH: Obama Calls Egypt’s Muslim Brotherhood President, ... http://cleowaller.blogspot.com/2013/02/obama-calls-egypts-muslim-brotherhood.html?spref=tw
"I Am One Of You" Obama Said To The Muslim Brotherhood
"I Am One Of You" Obama Said To The Muslim Brotherhood
Man at Pro-Second Amendment Rally Exposing the Obama Administration, Dri...: http://youtu.be/C_tVU0AmaQk via @youtube
Listen and wonder how such behavior can be tolerated on the part of a United States president. People are so uninformed and so complaisant. MORE FROM STEPHEN PIDGEON author of "The Obama Error" and "Behold! A White Horse." The radio segment is very long but also very informative. (bunch of anti-Catholic stuff at the end, just noting) A lot of scripture chopping and it fails to take note of the fulfillment of the covenant.
Mark Levin Explodes: ‘The Muslim Brotherhood Has Infiltrated Our Gov’t — It’s Called Barack Obama’
Mark Levin Explodes: ‘The Muslim Brotherhood Has Infiltrated Our Gov’t — It’s Called Barack Obama’
by Andrew Kirell | 1:16 pm, February 1st, 2013 audio » 291 comments“What the hell’s happening? Now we back the Muslim Brotherhood?” Levin said of the administration’s decision to aid Morsi.
The conservative radio host defended his “dear friends” Reps. Michele Bachmann (R-MN) and Louie Gohmert (R-TX) over their concerns that the administration has been “infiltrated” by the Muslim Brotherhood.
“[They] ask questions about the Muslim Brotherhood’s infiltration of our own government, and they’re treated like pariahs,” an agitated Levin shouted. “Well, the Muslim Brotherhood has infiltrated our government – it’s called Barack Obama! No, he’s not a formal member; he’s a sympathizer. There, I said it! Prove otherwise.”
Levin continued on trash Obama and his Defense Secretary nominee:
“You want to look into Obama’s soul? Well, look at his soul, you know what I see? I see Chuck Hagel. What kind of a commander-in-chief would nominate somebody like Chuck Hagel to be Secretary of Defense? I’ll tell you what kind of commander-in-chief: the kind of commander-in-chief that arms the Muslim Brotherhood, Islamo-Nazi regime in Cairo while he’s hollowing out the greatest military force on the face of the earth under his command, the United States military. That’s what kind of commander-in-chief!”The talk radio host then called Hagel an “Israel-hater” and a “sympathizer with the most radical elements of the Middle East” before declaring that “the president is Chuck Hagel” because he believes the same.
Accusing Jewish Democrats of being “lock-step” in supporting Hagel’s confirmation, Levin shouted, “It’s the righteous gentiles that are speaking up!”
Listen below, via WABC-NY:
[h/t The Right Scoop]
– –
>> Follow Andrew Kirell (@AndrewKirell) on Twitter
Obama Order Sped Up Wave of Cyberattacks Against Iran
Obama Order Sped Up Wave of Cyberattacks Against Iran
WASHINGTON — From his first months in office, President Obama secretly ordered increasingly sophisticated attacks on the computer systems that run Iran’s
main nuclear enrichment facilities, significantly expanding America’s
first sustained use of cyberweapons, according to participants in the
program.
Hasan Sarbakhshian/Associated Press
Iran’s nuclear enrichment facility at Natanz.
Multimedia
Mr. Obama decided to accelerate the attacks — begun in the Bush
administration and code-named Olympic Games — even after an element of
the program accidentally became public in the summer of 2010 because of a
programming error that allowed it to escape Iran’s Natanz plant and
sent it around the world on the Internet. Computer security experts who
began studying the worm, which had been developed by the United States
and Israel, gave it a name: Stuxnet.
At a tense meeting in the White House Situation Room within days of the
worm’s “escape,” Mr. Obama, Vice President Joseph R. Biden Jr. and the
director of the Central Intelligence Agency at the time, Leon E.
Panetta, considered whether America’s most ambitious attempt to slow the
progress of Iran’s nuclear efforts had been fatally compromised.
“Should we shut this thing down?” Mr. Obama asked, according to members
of the president’s national security team who were in the room.
Told it was unclear how much the Iranians knew about the code, and
offered evidence that it was still causing havoc, Mr. Obama decided that
the cyberattacks should proceed. In the following weeks, the Natanz
plant was hit by a newer version of the computer worm, and then another
after that. The last of that series of attacks, a few weeks after
Stuxnet was detected around the world, temporarily took out nearly 1,000
of the 5,000 centrifuges Iran had spinning at the time to purify
uranium.
This account of the American and Israeli effort to undermine the Iranian nuclear program
is based on interviews over the past 18 months with current and former
American, European and Israeli officials involved in the program, as
well as a range of outside experts. None would allow their names to be
used because the effort remains highly classified, and parts of it
continue to this day.
These officials gave differing assessments of how successful the
sabotage program was in slowing Iran’s progress toward developing the
ability to build nuclear weapons.
Internal Obama administration estimates say the effort was set back by
18 months to two years, but some experts inside and outside the
government are more skeptical, noting that Iran’s enrichment levels have
steadily recovered, giving the country enough fuel today for five or
more weapons, with additional enrichment.
Whether Iran is still trying to design and build a weapon is in dispute.
The most recent United States intelligence estimate concludes that Iran
suspended major parts of its weaponization effort after 2003, though
there is evidence that some remnants of it continue.
Iran initially denied that its enrichment facilities had been hit by
Stuxnet, then said it had found the worm and contained it. Last year,
the nation announced that it had begun its own military cyberunit, and
Brig. Gen. Gholamreza Jalali, the head of Iran’s Passive Defense
Organization, said that the Iranian military was prepared “to fight our
enemies” in “cyberspace and Internet warfare.” But there has been scant
evidence that it has begun to strike back.
The United States government only recently acknowledged developing
cyberweapons, and it has never admitted using them. There have been
reports of one-time attacks against personal computers used by members
of Al Qaeda, and of contemplated attacks against the computers that run
air defense systems, including during the NATO-led air attack on Libya
last year. But Olympic Games was of an entirely different type and
sophistication.
It appears to be the first time the United States has repeatedly used
cyberweapons to cripple another country’s infrastructure, achieving,
with computer code, what until then could be accomplished only by
bombing a country or sending in agents to plant explosives. The code
itself is 50 times as big as the typical computer worm, Carey
Nachenberg, a vice president of Symantec, one of the many groups that
have dissected the code, said at a symposium at Stanford University in
April. Those forensic investigations into the inner workings of the
code, while picking apart how it worked, came to no conclusions about
who was responsible.
A similar process is now under way to figure out the origins of another cyberweapon called Flame
that was recently discovered to have attacked the computers of Iranian
officials, sweeping up information from those machines. But the computer
code appears to be at least five years old, and American officials say
that it was not part of Olympic Games. They have declined to say whether
the United States was responsible for the Flame attack.
Mr. Obama, according to participants in the many Situation Room meetings
on Olympic Games, was acutely aware that with every attack he was
pushing the United States into new territory, much as his predecessors
had with the first use of atomic weapons in the 1940s, of
intercontinental missiles in the 1950s and of drones in the past decade.
He repeatedly expressed concerns that any American acknowledgment that
it was using cyberweapons — even under the most careful and limited
circumstances — could enable other countries, terrorists or hackers to
justify their own attacks.
“We discussed the irony, more than once,” one of his aides said. Another
said that the administration was resistant to developing a “grand
theory for a weapon whose possibilities they were still discovering.”
Yet Mr. Obama concluded that when it came to stopping Iran, the United
States had no other choice.
If Olympic Games failed, he told aides, there would be no time for
sanctions and diplomacy with Iran to work. Israel could carry out a
conventional military attack, prompting a conflict that could spread
throughout the region.
A Bush Initiative
The impetus for Olympic Games dates from 2006, when President George W. Bush
saw few good options in dealing with Iran. At the time, America’s
European allies were divided about the cost that imposing sanctions on
Iran would have on their own economies. Having falsely accused Saddam
Hussein of reconstituting his nuclear program in Iraq, Mr. Bush had
little credibility in publicly discussing another nation’s nuclear
ambitions. The Iranians seemed to sense his vulnerability, and,
frustrated by negotiations, they resumed enriching uranium at an
underground site at Natanz, one whose existence had been exposed just
three years before.
Iran’s president, Mahmoud Ahmadinejad, took reporters on a tour of the
plant and described grand ambitions to install upward of 50,000
centrifuges. For a country with only one nuclear power reactor — whose
fuel comes from Russia — to say that it needed fuel for its civilian
nuclear program seemed dubious to Bush administration officials. They
feared that the fuel could be used in another way besides providing
power: to create a stockpile that could later be enriched to bomb-grade
material if the Iranians made a political decision to do so.
Hawks in the Bush administration like Vice President Dick Cheney urged
Mr. Bush to consider a military strike against the Iranian nuclear
facilities before they could produce fuel suitable for a weapon. Several
times, the administration reviewed military options and concluded that
they would only further inflame a region already at war, and would have
uncertain results.
For years the C.I.A. had introduced faulty parts and designs into Iran’s
systems — even tinkering with imported power supplies so that they
would blow up — but the sabotage had had relatively little effect.
General James E. Cartwright, who had established a small cyberoperation
inside the United States Strategic Command, which is responsible for
many of America’s nuclear forces, joined intelligence officials in
presenting a radical new idea to Mr. Bush and his national security
team. It involved a far more sophisticated cyberweapon than the United
States had designed before.
The goal was to gain access to the Natanz plant’s industrial computer
controls. That required leaping the electronic moat that cut the Natanz
plant off from the Internet — called the air gap, because it physically
separates the facility from the outside world. The computer code would
invade the specialized computers that command the centrifuges.
The first stage in the effort was to develop a bit of computer code
called a beacon that could be inserted into the computers, which were
made by the German company Siemens and an Iranian manufacturer, to map
their operations. The idea was to draw the equivalent of an electrical
blueprint of the Natanz plant, to understand how the computers control
the giant silvery centrifuges that spin at tremendous speeds. The
connections were complex, and unless every circuit was understood,
efforts to seize control of the centrifuges could fail.
Eventually the beacon would have to “phone home” — literally send a message back to the headquarters of the National Security Agency
that would describe the structure and daily rhythms of the enrichment
plant. Expectations for the plan were low; one participant said the goal
was simply to “throw a little sand in the gears” and buy some time. Mr.
Bush was skeptical, but lacking other options, he authorized the
effort.
Breakthrough, Aided by Israel
It took months for the beacons to do their work and report home,
complete with maps of the electronic directories of the controllers and
what amounted to blueprints of how they were connected to the
centrifuges deep underground.
Then the N.S.A. and a secret Israeli unit respected by American
intelligence officials for its cyberskills set to work developing the
enormously complex computer worm that would become the attacker from
within.
The unusually tight collaboration with Israel was driven by two
imperatives. Israel’s Unit 8200, a part of its military, had technical
expertise that rivaled the N.S.A.’s, and the Israelis had deep
intelligence about operations at Natanz that would be vital to making
the cyberattack a success. But American officials had another interest,
to dissuade the Israelis from carrying out their own pre-emptive strike
against the Iranian nuclear facilities. To do that, the Israelis would
have to be convinced that the new line of attack was working. The only
way to convince them, several officials said in interviews, was to have
them deeply involved in every aspect of the program.
Soon the two countries had developed a complex worm that the Americans
called “the bug.” But the bug needed to be tested. So, under enormous
secrecy, the United States began building replicas of Iran’s P-1
centrifuges, an aging, unreliable design that Iran purchased from Abdul
Qadeer Khan, the Pakistani nuclear chief who had begun selling
fuel-making technology on the black market. Fortunately for the United
States, it already owned some P-1s, thanks to the Libyan dictator, Col.
Muammar el-Qaddafi.
When Colonel Qaddafi gave up his nuclear weapons program in 2003, he
turned over the centrifuges he had bought from the Pakistani nuclear
ring, and they were placed in storage at a weapons laboratory in
Tennessee. The military and intelligence officials overseeing Olympic
Games borrowed some for what they termed “destructive testing,”
essentially building a virtual replica of Natanz, but spreading the test
over several of the Energy Department’s national laboratories to keep
even the most trusted nuclear workers from figuring out what was afoot.
Those first small-scale tests were surprisingly successful: the bug
invaded the computers, lurking for days or weeks, before sending
instructions to speed them up or slow them down so suddenly that their
delicate parts, spinning at supersonic speeds, self-destructed. After
several false starts, it worked. One day, toward the end of Mr. Bush’s
term, the rubble of a centrifuge was spread out on the conference table
in the Situation Room, proof of the potential power of a cyberweapon.
The worm was declared ready to test against the real target: Iran’s
underground enrichment plant.
“Previous cyberattacks had effects limited to other computers,” Michael
V. Hayden, the former chief of the C.I.A., said, declining to describe
what he knew of these attacks when he was in office. “This is the first
attack of a major nature in which a cyberattack was used to effect
physical destruction,” rather than just slow another computer, or hack
into it to steal data.
“Somebody crossed the Rubicon,” he said.
Getting the worm into Natanz, however, was no easy trick. The United
States and Israel would have to rely on engineers, maintenance workers
and others — both spies and unwitting accomplices — with physical access
to the plant. “That was our holy grail,” one of the architects of the
plan said. “It turns out there is always an idiot around who doesn’t
think much about the thumb drive in their hand.”
In fact, thumb drives turned out to be critical in spreading the first
variants of the computer worm; later, more sophisticated methods were
developed to deliver the malicious code.
The first attacks were small, and when the centrifuges began spinning
out of control in 2008, the Iranians were mystified about the cause,
according to intercepts that the United States later picked up. “The
thinking was that the Iranians would blame bad parts, or bad
engineering, or just incompetence,” one of the architects of the early
attack said.
The Iranians were confused partly because no two attacks were exactly
alike. Moreover, the code would lurk inside the plant for weeks,
recording normal operations; when it attacked, it sent signals to the
Natanz control room indicating that everything downstairs was operating
normally. “This may have been the most brilliant part of the code,” one
American official said.
Later, word circulated through the International Atomic Energy Agency,
the Vienna-based nuclear watchdog, that the Iranians had grown so
distrustful of their own instruments that they had assigned people to
sit in the plant and radio back what they saw.
“The intent was that the failures should make them feel they were
stupid, which is what happened,” the participant in the attacks said.
When a few centrifuges failed, the Iranians would close down whole
“stands” that linked 164 machines, looking for signs of sabotage in all
of them. “They overreacted,” one official said. “We soon discovered they
fired people.”
Imagery recovered by nuclear inspectors from cameras at Natanz — which
the nuclear agency uses to keep track of what happens between visits —
showed the results. There was some evidence of wreckage, but it was
clear that the Iranians had also carted away centrifuges that had
previously appeared to be working well.
But by the time Mr. Bush left office, no wholesale destruction had been
accomplished. Meeting with Mr. Obama in the White House days before his
inauguration, Mr. Bush urged him to preserve two classified programs,
Olympic Games and the drone program in Pakistan. Mr. Obama took Mr.
Bush’s advice.
The Stuxnet Surprise
Mr. Obama came to office with an interest in cyberissues, but he had
discussed them during the campaign mostly in terms of threats to
personal privacy and the risks to infrastructure like the electrical
grid and the air traffic control system. He commissioned a major study
on how to improve America’s defenses and announced it with great fanfare
in the East Room.
What he did not say then was that he was also learning the arts of cyberwar.
The architects of Olympic Games would meet him in the Situation Room,
often with what they called the “horse blanket,” a giant foldout
schematic diagram of Iran’s nuclear production facilities. Mr. Obama
authorized the attacks to continue, and every few weeks — certainly
after a major attack — he would get updates and authorize the next step.
Sometimes it was a strike riskier and bolder than what had been tried
previously.
“From his first days in office, he was deep into every step in slowing
the Iranian program — the diplomacy, the sanctions, every major
decision,” a senior administration official said. “And it’s safe to say
that whatever other activity might have been under way was no exception
to that rule.”
But the good luck did not last. In the summer of 2010, shortly after a
new variant of the worm had been sent into Natanz, it became clear that
the worm, which was never supposed to leave the Natanz machines, had
broken free, like a zoo animal that found the keys to the cage. It fell
to Mr. Panetta and two other crucial players in Olympic Games — General
Cartwright, the vice chairman of the Joint Chiefs of Staff, and Michael
J. Morell, the deputy director of the C.I.A. — to break the news to Mr.
Obama and Mr. Biden.
An error in the code, they said, had led it to spread to an engineer’s
computer when it was hooked up to the centrifuges. When the engineer
left Natanz and connected the computer to the Internet, the American-
and Israeli-made bug failed to recognize that its environment had
changed. It began replicating itself all around the world. Suddenly, the
code was exposed, though its intent would not be clear, at least to
ordinary computer users.
“We think there was a modification done by the Israelis,” one of the
briefers told the president, “and we don’t know if we were part of that
activity.”
Mr. Obama, according to officials in the room, asked a series of
questions, fearful that the code could do damage outside the plant. The
answers came back in hedged terms. Mr. Biden fumed. “It’s got to be the
Israelis,” he said. “They went too far.”
In fact, both the Israelis and the Americans had been aiming for a
particular part of the centrifuge plant, a critical area whose loss,
they had concluded, would set the Iranians back considerably. It is
unclear who introduced the programming error.
The question facing Mr. Obama was whether the rest of Olympic Games was
in jeopardy, now that a variant of the bug was replicating itself “in
the wild,” where computer security experts can dissect it and figure out
its purpose.
“I don’t think we have enough information,” Mr. Obama told the group
that day, according to the officials. But in the meantime, he ordered
that the cyberattacks continue. They were his best hope of disrupting
the Iranian nuclear program unless economic sanctions began to bite
harder and reduced Iran’s oil revenues.
Within a week, another version of the bug brought down just under 1,000 centrifuges. Olympic Games was still on.
A Weapon’s Uncertain Future
American cyberattacks are not limited to Iran, but the focus of
attention, as one administration official put it, “has been
overwhelmingly on one country.” There is no reason to believe that will
remain the case for long. Some officials question why the same
techniques have not been used more aggressively against North Korea.
Others see chances to disrupt Chinese military plans, forces in Syria on
the way to suppress the uprising there, and Qaeda operations around the
world. “We’ve considered a lot more attacks than we have gone ahead
with,” one former intelligence official said.
Mr. Obama has repeatedly told his aides that there are risks to using —
and particularly to overusing — the weapon. In fact, no country’s
infrastructure is more dependent on computer systems, and thus more
vulnerable to attack, than that of the United States. It is only a
matter of time, most experts believe, before it becomes the target of
the same kind of weapon that the Americans have used, secretly, against
Iran.
Clinton waives terror restrictions, gives Pakistan $2 BILLION more US taxpayer dollars
Clinton waives terror restrictions, gives Pakistan $2 BILLION more US taxpayer dollars
Posted on October 12, 2012 by creeping
via Pakistan freed of anti-terrorism obligations; U.S. billions flow instead – KansasCity.com.
The Obama administration has refused for
the first time to declare that Pakistan is making progress toward ending
alleged military support for Islamic militant groups or preventing al
Qaida, the Afghan Taliban or other extremists from staging attacks in
Afghanistan.
Even so, Secretary of State Hillary
Clinton has quietly informed Congress that she’s waived the legal
restrictions that would have blocked some $2 billion in U.S. economic
and military aid to Pakistan. Disbursing the funds, she said in an official notice, is “important to the national security interests of the United States.”
Clinton’s decision illustrates how far the
administration apparently has determined that it must go, after a
near-breakdown in relations, to ensure Pakistan’s cooperation in the
uphill U.S. effort to prevent Afghanistan collapsing into all-out civil
war when American-led international combat forces complete a withdraw by
the end of 2014.
Some experts, however, warned that the
move might backfire. The waivers could encourage a belief among
Pakistani commanders that their cooperation is so crucial that
Washington will continue overlooking the Pakistani military’s refusal to
end what U.S. officials charge is its support for Afghan insurgent
groups or to shutter militant sanctuaries, they said.
“The army is going to think that no matter
how angry the Americans are at them, they are utterly indispensable and
they can violate in any way, shape or form U.S. law and the United
States will massage its law to accommodate them,” said assistant
professor Christine Fair, an expert at Georgetown University. “That’s
how they are going to read this.”
Yep. Just like the Muslim world views the arrest of the so-called Muhammad film maker as Obama enforcing Islamic blasphemy laws.
Leak of top secret Stuxnet program could provide grounds for impeachment
Leak of top secret Stuxnet program could provide grounds for impeachment
The left-leaning Washington Post explains.Excerpt:
Imagine if The Post broke a story about the biggest scandal of the Obama-era — and Washington responded with a collective yawn?I wouldn’t put it past Obama to leak sensitive data to help his election campaign. If you check the related links below, you’ll see that the Obama administration is just awful at national security.
That’s precisely what happened recently when The Post reported on its front page that senior Obama administration officials were being investigated by the FBI and Justice Department for the leak last summer that the president had personally ordered cyberattacks on the Iranian nuclear program using a computer virus developed with Israel called Stuxnet.
The Post quotes a source who says that FBI agents and prosecutors are pursuing “everybody — at pretty high levels.” The paper further reports that investigators “have conducted extensive analysis of the e-mail accounts and phone records of current and former government officials” and that some have been confronted “with evidence of contact with journalists.”
This is big. And former senior government lawyers I spoke with recently explained why it could get a whole lot bigger:
The leaks clearly came from someone in the president’s inner circle. As The Post explains, “Knowledge of the virus was likely to have been highly compartmentalized and limited to a small set of Americans and Israelis.” Moreover, whoever leaked the information was present when the president discussed this covert action program in the Situation Room. There is a tiny universe of individuals who could have shared the details of President Obama’s personal deliberations on the covert program with the press.
[...][T]he Stuxnet leak was incredibly damaging. It exposed intelligence sources and methods, including the top secret codename for the program (“Olympic Games”). And it exposed the involvement of a U.S. ally, Israel. At one point in the New York Times story, a source says the Israelis were responsible for an error in the code who allowed it to replicate itself all around the world. The Times directly quotes one of the president’s briefers telling him “We think there was a modification done by the Israelis,” adding that “Mr. Obama, according to officials in the room, asked a series of questions, fearful that the code could do damage outside the plant. The answers came back in hedged terms. Mr. Biden fumed. ‘It’s got to be the Israelis,’ he said. ‘They went too far’” (emphasis added).
So a person who was “in the room” when the president and vice president were briefed publicly confirmed Israeli involvement in a covert action against Iran. The damage this did — both to the operation and the trust between our two countries — is incalculable.
There are no credible national security grounds for such a disclosure. The only person whose interests could possibly be served by such a disclosure was Obama. The leak appeared six months before the president stood for reelection and was clearly intended to make Obama appear strong on foreign policy and counterterrorism. (One anonymous senior official is quoted by the Times as saying “From his first days in office, he was deep into every step in slowing the Iranian program — the diplomacy, the sanctions, every major decision.”)
If the president authorized the disclosure of national security secrets that exposed a covert action and undermined a U.S. ally in an effort to gain a political advantage in his reelection campaign, that would be a scandal of gigantic proportions. As one former top Justice Department official told me “if done for political gain, rather than for a bona fide purpose advancing the public interests of the United States, it could be grounds for impeachment.”
Related posts
- White House told that terrorists took credit for Benghazi attack within two hours
- Obama covers-up DOJ operation that allowed gun smuggling to Mexican drug cartels
- Obama administration leaked name of British agent who stopped Al Qaeda attack
- Obama’s neutrality on the Falklands dispute puts special relationship at risk
- Is the Obama administration behind the leak of Israel’s plan to strike Iran?
- Is Obama promising the Russians more unilateral disarmament after the election?
- Iran set to steal military technology from the drone Obama gave them
Subscribe to:
Comments (Atom)