Moti Yung and Adam Young on Kleptography and Cryptovirology 3: Deploying Cryptoviral Extortion Attack
Posted by david b. on January 31, 2013
In this part, Moti Yung lists the main possible applications
for cryptovirology and goes into detail of a typical cryptoviral
extortion attack.Now we’re going to get to the subject of cryptovirology, and I will review three topics (see image). The first one is cryptoviral extortion; this is an active attack. The second subject that I will cover will be deniable password snatching, which is a passive attack where the combination of cryptographic technology and other available modern channels, that are available in the infrastructure, enables us to provide the attacker with deniability of being identified. And the third topic that I’ll just mention is computationally secure information stealing: kind of when you know the virus, you have all the traces of the operation, and still you don’t know what the virus was stealing.
So, these are the types of things you can do when you start combining these technologies: this public-key cryptography on the one hand, and viruses on the other. How can such research be justified? Well, actually I don’t think this is the right conference; I should have erased this slide (see left-hand image). Everybody understands: you have to hack systems, you have to break systems, you have to think about threats, and this will help society if you get the right cooperation, and I’ll talk about it later.
An Insight into Cryptoviral Extortion
Let’s go directly to the setting of the cryptoviral extortion (see image to the right). Assume the following setting: the host computer has valuable data, I call it D, and due to the usual laziness it’s not backed up, or not fully backed up at the moment. And assume you wrote a virus that has access to secure random bit generator; it has entropy extraction in it, it can read the environment and get kind of truly random bits from the physical devices. The virus has a code for secure symmetric cipher like AES. And the virus has access to code for secure asymmetric cipher; this is the public-key encryption, so this is a program for, let’s say, RSA encryption.Here is, more or less, the cryptoviral extortion attack (see left-hand image), and this is a protocol between the attacker and the virus. Let’s go see what’s going on here. So, the attacker generates a private key x and corresponding public key y, and the attacker places y in the virus, but keeps x to himself in his own machine not connected to anything, nothing, not the Internet, not anything. And then the virus arrives at the host machine, and, as I said, this is not a part of the talk: “how to get there,” but we got it, it’s there. So, what does it do there? It activates, it generates a random symmetric key k, a key for AES, decrypts the big file D with this key k, obtains C, so C is the encryption of D under AES, and then encrypts the key k that was used in this encryption with the public key y to obtain the ciphertext – c.
The virus deletes the data D and the key k, and then informs the victim of the attack, gives contact information to the attacker, hopefully not directly, but some digital information, some anonymous Swiss bank account. And then the victim contacts the attacker and gives the attacker c along with the ransom, because it asked for some money in step 4.
Step 5 – the attacker obtains the ransom, and since he wants to play nice, at this point he can run away with the ransom, but if he’s smart and he wants to be in business, he should take c, use x which is the asymmetric key that he has, that he is the one that has the ability to decrypt with it, and from c using the key x obtains k. The key k is sent to the victim, and then the victim in step 6, having obtained k, can decrypt C and get the data D. So, you see what happens: somehow there’s this game that we designed.
So, first of all, security of this attack (see right-hand image): analyzing the code of the virus reveals the public key y and not the private key x, because it’s not there. Just knowing the encryption key y is not sufficient for decryption. As long as the symmetric key k is not captured and the virus is written right, then in short time it is erased after the decryption, and there’s no way to recover k, because it exists only in encrypted form. The encryption can also be performed incrementally if you want to avoid detection, this is virus technology. And then there are variations: you don’t necessarily have to extort money, you can get data and the like. Communication can be done in an anonymous way, and so on. So, this gives security to the attacker. That was a way to show that the power of public-key cryptography is such that there are really unequal powers here: the attacker has the decryption key, and he’s the only one that has the decryption key. And he has to be involved in the recovery.
So, before the involvement of public key such imbalance of power between the attacker and the attacked host did not exist, and this is the right tool for this imbalance of power. So, previously the virus could disrupt, could delete things and so on, but never move the power to release the information to the attacker who is remote and is not even present while the virus is operating. Ok, that’s the first idea.
To be continued…
Read previous: Moti Yung and Adam Young on Kleptography and Cryptovirology 2: Cryptography in Polymorphic Viruses
Moti Yung and Adam Young on Kleptography and Cryptovirology 2: Cryptography in Polymorphic Viruses
Posted by david b. on January 30, 2013
Continuing with the retrospective overview of malicious
software, in this part Moti Yung focuses on the role of crypto in the
execution workflow of polymorphic viruses and touches upon the basic
principles of public-key cryptography.I want to point out one interesting design – actually, implementation in design from the 1980s, and this is the survivable Trojan horse of Ken Thompson created in 1984. He described it in his Turing Award lecture. What he designed is, effectively, a survivable password snatching Trojan horse. Password snatcher is a program that tries to infect the Unix password program, and the design goal is to show how systems are getting complex and threats are getting serious. He designed a Trojan horse that survived recompilation and reinstallation of the password program on the host machine.
He demonstrated that it’s not just the application itself that needs to be protected, and I have the description here but I will skip it, but I’ll get to the bottom line. The bottom line was that, essentially, the Trojan was using the C compiler to increase its survivability; and then if you replace the C compiler or the password program, just the smart operation of this Trojan made it survive and replicate inside the system. So, the bottom line of this was that one cannot just scrutinize the trustworthiness of a program by analyzing the source code and by compiling it – in some sense, the entire machine must be scrutinized, because he used something that was hiding in the compiler, therefore the source code, the compiler, linker, assembler, operating system need to be analyzed. When the threat comes from one source, you cannot just go there; really, it spreads around.
The academic studies by Cohen in his PhD thesis in the 1980s: he started to investigate viral countermeasures and bypassing these countermeasures. What he noted is the idea that a virus can change itself in the replication process. He produced some viruses that had no common sequence of over 3 bytes between each generation, and he called them evolutionary viruses, and nowadays we know about polymorphic viruses.
Also in the 1980s it was shown that the problem of whether a program or a set of programs has a virus or doesn’t have a virus is undecidable; the meaning is there is no universal treatment, and at the same time the antivirus heuristics based on scanning and signatures started to be developed. Another thing that happened in the 80s is worms were invented as a paradigm for distributed computing in Xerox PARC, among other innovations.
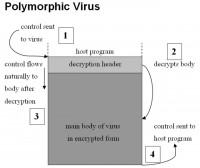
And, as I said, polymorphic viruses are now known threats, and they employ cryptography, to begin with. I’m not getting into details, but there is a decryption header that decrypts the program (see left-hand image), the program can execute when there is a replication. The decryption can be done with another key. So, you can see how cryptography can generate many viewpoints of the same encrypted piece of software. This was already something that existed as application of cryptography to malware when we started. So, you can do many changes, and it’s easy to exponentially explore the space of possible viruses, and this was noticed in the early 90s.
This was the state of the art when we started; the other piece of the picture that we wanted to include in our technology is public-key cryptography (see right-hand image). For the sake of this presentation, I’m not going to dwell a lot on public-key cryptography. But all you have to know is that there is a public key denoted Y there, and it has a corresponding secret key X; X is kept by the key owner. Everybody can encrypt E of Y in the message, get the ciphertext CI, everybody can decrypt it. But the knowledge of Y does not enable the decryption of the ciphertext back to the message. Only the one who knows X, this is called Trapdoor Information, can take the ciphertext and the secret key X, apply a transformation denoted D, which is the reverse operation to the encryption, and get the message back.
So, this is the idea from the late 70s, and the first example of it was the RSA which was based on factoring big numbers: there is a number N that is a multiple of P and Q, two big numbers, and you cannot factor them, you cannot take the root; therefore you can take the message and raise it to the E mod N; only if you can factor, you can recover them. Applications for this are encryption, key exchange, digital signatures, and various protocols that have been suggested in the last 30 years, like playing poker over the phone, etc.
Read previous: “Yes We Can’t!” – On Kleptography and Cryptovirology
Read next: Moti Yung and Adam Young on Kleptography and Cryptovirology 3: Deploying Cryptoviral Extortion Attack
Moti Yung and Adam Young on Kleptography and Cryptovirology 3: Deploying Cryptoviral Extortion Attack
Posted by david b. on January 31, 2013
In this part, Moti Yung lists the main possible applications
for cryptovirology and goes into detail of a typical cryptoviral
extortion attack.Now we’re going to get to the subject of cryptovirology, and I will review three topics (see image). The first one is cryptoviral extortion; this is an active attack. The second subject that I will cover will be deniable password snatching, which is a passive attack where the combination of cryptographic technology and other available modern channels, that are available in the infrastructure, enables us to provide the attacker with deniability of being identified. And the third topic that I’ll just mention is computationally secure information stealing: kind of when you know the virus, you have all the traces of the operation, and still you don’t know what the virus was stealing. So, these are the types of things you can do when you start combining these technologies: this public-key cryptography on the one hand, and viruses on the other. How can such research be justified? Well, actually I don’t think this is the right conference; I should have erased this slide (see left-hand image). Everybody understands: you have to hack systems, you have to break systems, you have to think about threats, and this will help society if you get the right cooperation, and I’ll talk about it later.
An Insight into Cryptoviral Extortion
Let’s go directly to the setting of the cryptoviral extortion (see image to the right). Assume the following setting: the host computer has valuable data, I call it D, and due to the usual laziness it’s not backed up, or not fully backed up at the moment. And assume you wrote a virus that has access to secure random bit generator; it has entropy extraction in it, it can read the environment and get kind of truly random bits from the physical devices. The virus has a code for secure symmetric cipher like AES. And the virus has access to code for secure asymmetric cipher; this is the public-key encryption, so this is a program for, let’s say, RSA encryption. Here is, more or less, the cryptoviral extortion attack (see left-hand image), and this is a protocol between the attacker and the virus. Let’s go see what’s going on here. So, the attacker generates a private key x and corresponding public key y, and the attacker places y in the virus, but keeps x to himself in his own machine not connected to anything, nothing, not the Internet, not anything. And then the virus arrives at the host machine, and, as I said, this is not a part of the talk: “how to get there,” but we got it, it’s there. So, what does it do there? It activates, it generates a random symmetric key k, a key for AES, decrypts the big file D with this key k, obtains C, so C is the encryption of D under AES, and then encrypts the key k that was used in this encryption with the public key y to obtain the ciphertext – c.The virus deletes the data D and the key k, and then informs the victim of the attack, gives contact information to the attacker, hopefully not directly, but some digital information, some anonymous Swiss bank account. And then the victim contacts the attacker and gives the attacker c along with the ransom, because it asked for some money in step 4.
Step 5 – the attacker obtains the ransom, and since he wants to play nice, at this point he can run away with the ransom, but if he’s smart and he wants to be in business, he should take c, use x which is the asymmetric key that he has, that he is the one that has the ability to decrypt with it, and from c using the key x obtains k. The key k is sent to the victim, and then the victim in step 6, having obtained k, can decrypt C and get the data D. So, you see what happens: somehow there’s this game that we designed.
So, first of all, security of this attack (see right-hand image): analyzing the code of the virus reveals the public key y and not the private key x, because it’s not there. Just knowing the encryption key y is not sufficient for decryption. As long as the symmetric key k is not captured and the virus is written right, then in short time it is erased after the decryption, and there’s no way to recover k, because it exists only in encrypted form. The encryption can also be performed incrementally if you want to avoid detection, this is virus technology. And then there are variations: you don’t necessarily have to extort money, you can get data and the like. Communication can be done in an anonymous way, and so on. So, this gives security to the attacker. That was a way to show that the power of public-key cryptography is such that there are really unequal powers here: the attacker has the decryption key, and he’s the only one that has the decryption key. And he has to be involved in the recovery.
So, before the involvement of public key such imbalance of power between the attacker and the attacked host did not exist, and this is the right tool for this imbalance of power. So, previously the virus could disrupt, could delete things and so on, but never move the power to release the information to the attacker who is remote and is not even present while the virus is operating. Ok, that’s the first idea.
To be continued…
Read previous: Moti Yung and Adam Young on Kleptography and Cryptovirology 2: Cryptography in Polymorphic Viruses









No comments:
Post a Comment