Hackers take aim at key U.S. infrastructure
@CNNMoney February 20, 2013: 3:59 PM ET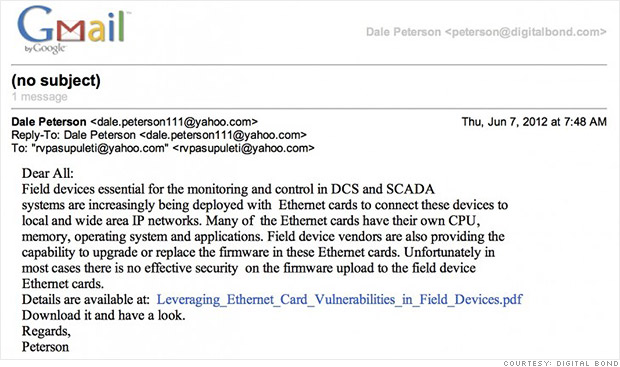 This "spear phishing" email was received by one infrastructure
security firm. It appears to come from the firm's CEO, but is actually
from an attacker trying to trick recipients into clicking on a malicious
link.
This "spear phishing" email was received by one infrastructure
security firm. It appears to come from the firm's CEO, but is actually
from an attacker trying to trick recipients into clicking on a malicious
link.
NEW YORK (CNNMoney)
Tuesday's report detailing hacking activities by the Chinese government against U.S. targets all but confirmed what everyone suspected: the Chinese, along with other nations and groups, are gathering information that could disrupt the operation of critical infrastructure in this country, including power plants, chemical factories and air-traffic control systems.
To be clear, the report from U.S.-based cybersecurity firm Mandiant did not say the Chinese government has actively tampered with these systems. The only two countries thought to have actually altered industrial processes in another country are the United States and Israel, which are suspected of infecting an Iranian uranium enrichment plant with malicious software that caused the centrifuges to spin out of control and self-destruct.Mandiant's analysis fingering the Chinese comes just two months after the U.S. Department of Homeland Security said cyber attacks on critical U.S. infrastructure jumped 52% last year. The department fielded reports on 198 attacks, several of which resulted in successful break-ins.
Related: Wake up, America! China is attacking
Experts say the snooping probably has two purposes: To gather information in an effort to improve China's own critical infrastructure; and to lay the groundwork for a future attack to shut down those systems, if China wanted to pursue that option.
If it did ever come to that, things could get ugly in short order.
The industrial control systems than run so many of America's power plants, factories, pipelines, dams, water treatment plants and other infrastructure elements are fairly well guarded from the outside, said Dale Peterson, chief executive of Digital Bond, a company that consults on such matters. But once a hacker is in the system, Peterson said there's very few safeguards preventing the intruder from sending commands that could, say, cause an accident at a chemical plant or lead a pharmaceutical factory to dispense the wrong medications.
"Once they get on those networks, they are insecure by design," he said.
Targeting a third-party vendor like Telvent is one way to get around the more robust security systems put in place by the pipeline companies, Peterson said. Telvent, as a contractor, had access to the pipeline networks.
Targeting third parties is something Petersen has experience with himself: His own firm was the subject of a so-called "spear phishing" attempt last year. In that attack, a crafty cyberthief fashioned an email to Digital Bond employees that seemed to come from Petersen himself (see graphic at top). It contained a link that, if clicked on, could have granted the perpetrator access to sensitive client data held by Digital Bond. The plan was only thwarted when an auto-forward function sent Petersen a copy.
"For a while, it was a dirty little secret that just people in the industry knew," said Petersen, referring to how easy it is to take over an industrial process once you're in the system. "But we can't wait another 20 years, or whatever it is that people thought we could get out of these systems. We have to upgrade them now."
The attack on Digital Bond appeared to originate from China, Petersen said. The key word there, though, is "appeared." The perpetrators could have designed the attack to look like it came from China, he acknowledged.
So far, said Petersen, neither the government nor the private sector is doing enough.
One of the most critical systems is the power grid. Without electricity, factories, water delivery and offices all stop working.
Electric industry sources say the most sensitive equipment -- think nuclear power plants -- have internal, on-site control functions that are not connected to the Internet. That makes them much less vulnerable to attack.
But not all systems are that secure. The advanced age of much of the power grid, combined with how interconnected everything is, is a major challenge.
"It's an issue that's at the top of the list of every utility executive," said Mark McGranaghan, a power delivery and utilization specialist at the Electric Power Research Institute.
McGranaghan said building redundancies into the system should make it stronger. There are also efforts toward greater monitoring, and toward ensuring that compromised systems can be isolated. He believes grid security should be made better, not worse, by the adoption of smart meters and other Internet-connected devices that could further the utilities' ability is quickly wall-off problem
Still, he conceded that challenges remain.
"There will be breaches, and it's a very interconnected system," he said. Problems "can result in cascading conditions."
No comments:
Post a Comment