arget : Cross Site Scripting (XSS) Vulnerable website
According to wikipedia.org Cross Site Scripting (XSS) is :
Actually there's 2 types of Cross Site Scripting (XSS) : Non-Persistent and Persistent (you can read it more at wikipedia), but in this tutorial we will learn about the non-persistent one.
One of my computer security class student 3 years ago ask me about "what will I got if I successfully found a vulnerable XSS website?", I simply can answer "it's depend"; yes it is depend on how the server handle your request and how they take care the malicious data you provide to the server, but the non-persistent one is great enough to spread a malicious file to many internet users.
Let's start the tutorial…
Requirements :
1. Found a Cross Site Scripting (XSS) vulnerable website, or
2. You can download the simple PHP file I have already create below (download link)
Step by Step :
1. You can use the PHP file I already put on mediafire.com for you test it on your own lab(use XAMPP), but for this tutorial I will use from real website on the wild internet (do not worry, the logic was the same, once you understand it you'll got the point)
2. Use Google to search for vulnerable website :
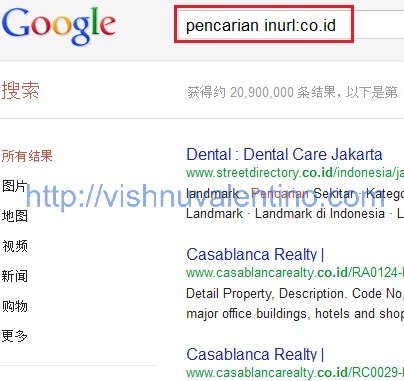
Pencarian was Indonesian language equal to searching, you can modify the Google parameter for search the much more specific website even in your own language.
3. To find a vulnerable website, you need to do a trial and error. I'm testing more than 5 website to test for their search feature is it vulnerable or not for XSS.
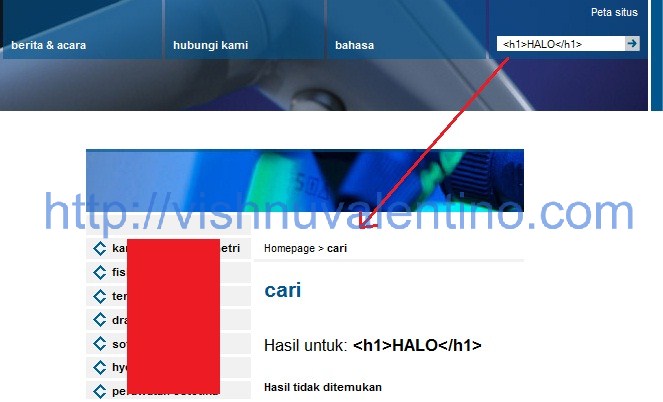
The simple method to test was using <h1> and <script>alert('x');</script> tag like example picture above.
4. If the website was vulnerable, you will find something like this.
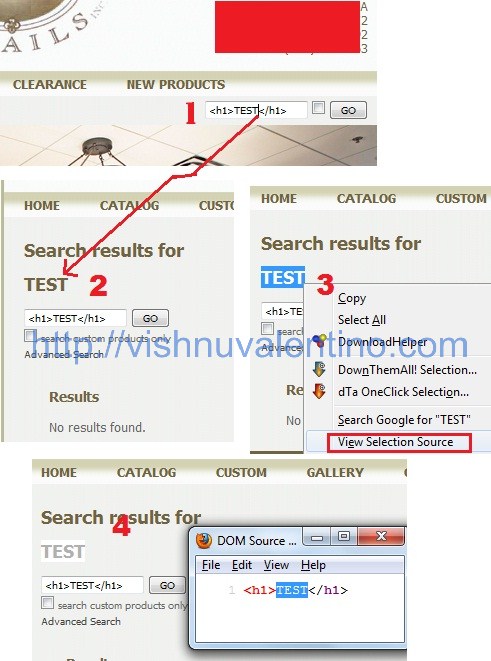
Description :
- See more at: http://www.hacking-tutorial.com/hacking-tutorial/basic-hacking-via-cross-site-scripting-xss-the-logic/#sthash.tKN5oGzh.dpuf
According to wikipedia.org Cross Site Scripting (XSS) is :
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in Web applications, such as web browsers through breaches of browser security, that enables attackers to inject client-side script into Web pages viewed by other users.So let say that Cross Site Scripting (XSS) was a hacking method that allow attacker inject some script to web server that can affect other users that accessing that webpage.
Actually there's 2 types of Cross Site Scripting (XSS) : Non-Persistent and Persistent (you can read it more at wikipedia), but in this tutorial we will learn about the non-persistent one.
One of my computer security class student 3 years ago ask me about "what will I got if I successfully found a vulnerable XSS website?", I simply can answer "it's depend"; yes it is depend on how the server handle your request and how they take care the malicious data you provide to the server, but the non-persistent one is great enough to spread a malicious file to many internet users.
Let's start the tutorial…
Requirements :
1. Found a Cross Site Scripting (XSS) vulnerable website, or
2. You can download the simple PHP file I have already create below (download link)
| Mediafire.com |
Step by Step :
1. You can use the PHP file I already put on mediafire.com for you test it on your own lab(use XAMPP), but for this tutorial I will use from real website on the wild internet (do not worry, the logic was the same, once you understand it you'll got the point)
2. Use Google to search for vulnerable website :

Pencarian was Indonesian language equal to searching, you can modify the Google parameter for search the much more specific website even in your own language.
3. To find a vulnerable website, you need to do a trial and error. I'm testing more than 5 website to test for their search feature is it vulnerable or not for XSS.

The simple method to test was using <h1> and <script>alert('x');</script> tag like example picture above.
4. If the website was vulnerable, you will find something like this.

Description :
1. I test other website and input the code <h1>TEST</h1> or <script>alert('x');</script> on search box.
2. The result was show a heading title, but I'm not sure, then
3. I check the selection source to make sure it's not a bold :-p
4. Oops..my query was purely processed by server without filtering 
5. Now we got the vulnerable website what to do next?? Did you know that with Cross Site Scripting (XSS) you also can do a defacing to a website by injecting some code in it?(not really deface/fake)
- See more at: http://www.hacking-tutorial.com/hacking-tutorial/basic-hacking-via-cross-site-scripting-xss-the-logic/#sthash.tKN5oGzh.dpuf
No comments:
Post a Comment